The State of Internet Security in 2020
2020 started off relatively well in the cybersecurity realm. The fintech industry in particular finally had come to their senses and begun to implement common-sense security controls. As we all know, just a few months into the year, economies around the world hit a major snag: COVID-19.
Many countries and states in the US required business and public facility closures for extended periods of time and encouraged people to stay home. As a result, a large shift in consumption occurred, with consumers spending far more time online. The recent record highs set by many tech stocks reflects this new change in global spending habits. For example the ROI on a Microsoft share in 2020 was a whopping 32%. The only major tech company to not see significant gains was Google, largely due to antitrust suit issues.
2020 was a perfect storm for one of the worst years for cybersecurity in history. With an unprecedented amount of users online, servers were already overloaded, making DDoS attacks require far less bandwidth. Given that states doled out billions of dollars of funds from the CARES Act to unemployed people, a massive fraud target was created.
A tense international political landscape has also contributed to the situation. Let’s take a look at the specifics.
The Research Behind the Madness
Researchers at Akamai were the first to discover that cyber criminals were reusing phishing kits in record numbers after COVID-19 hit[1]. These are often available on publicly accessible hacking forums and various dark web markets cheaply. In previous years, phishing kits were rarely recycled.
Why the difference this year? Many people had high levels of anxiety surrounding their health and finances. The key element behind any successful social engineering attempt is fear of a consequence occurring if the request isn’t executed. This is how many identities were stolen, the majority of which were used to commit unemployment insurance fraud on massive scales.
Phishing kits weren’t the only items reused to steal information. Relatively speaking, this was a minor problem on the cybersecurity landscape. The true issues this year predominantly stemmed from credential stuffing, password reuse, and enterprise failures to change default passwords. Let’s take a look at some of the most prolific incidents that happened.
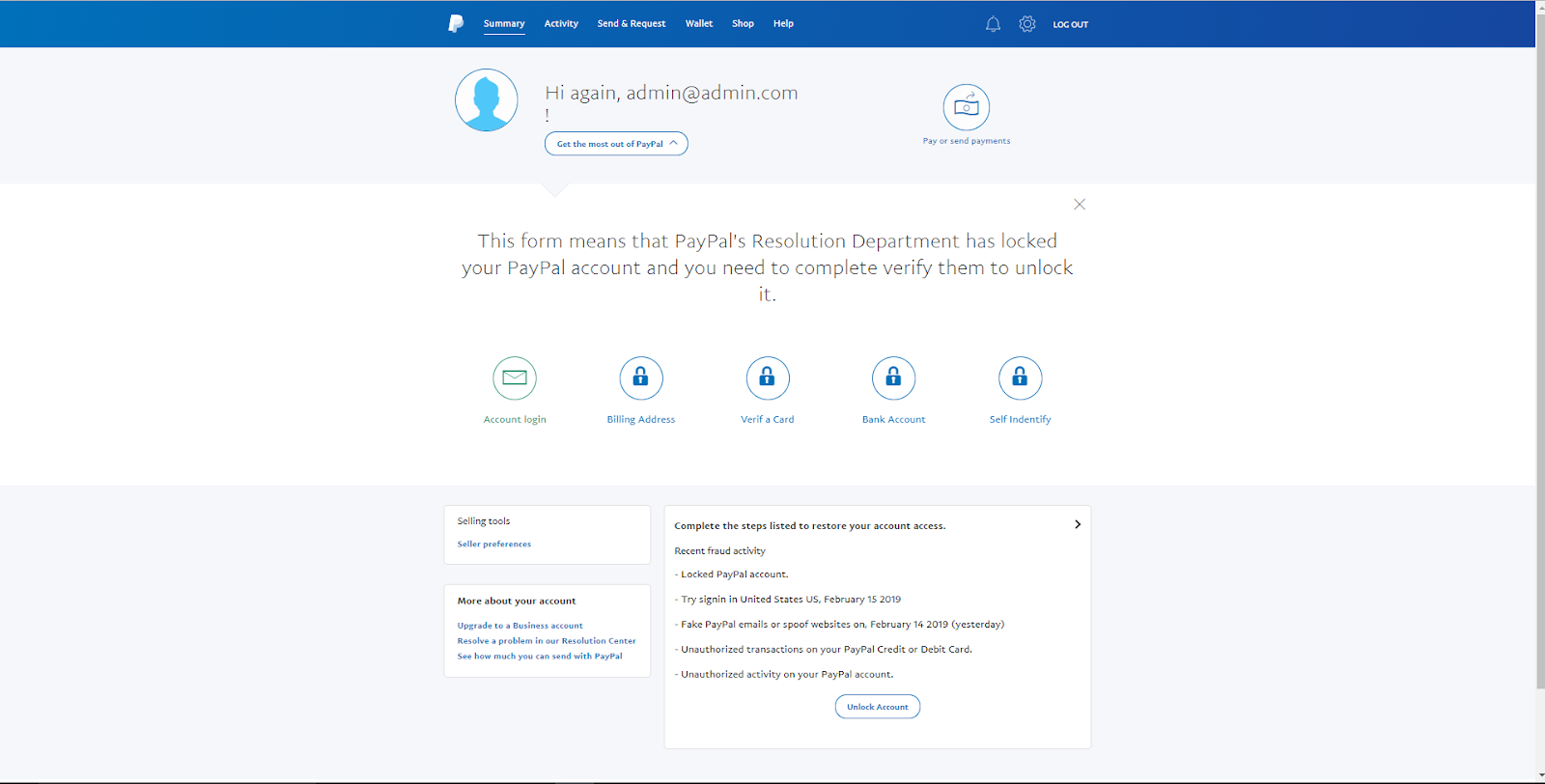
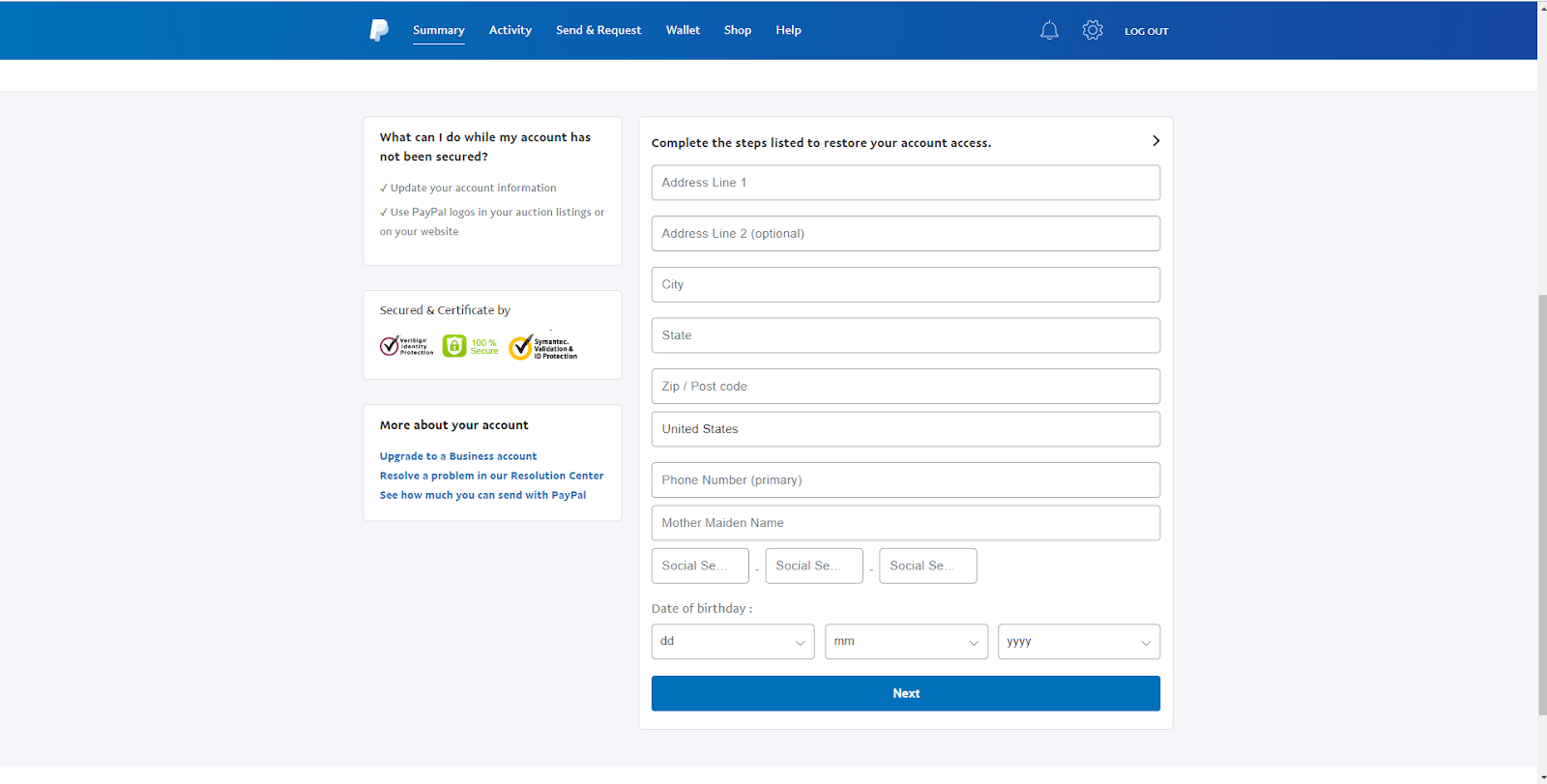
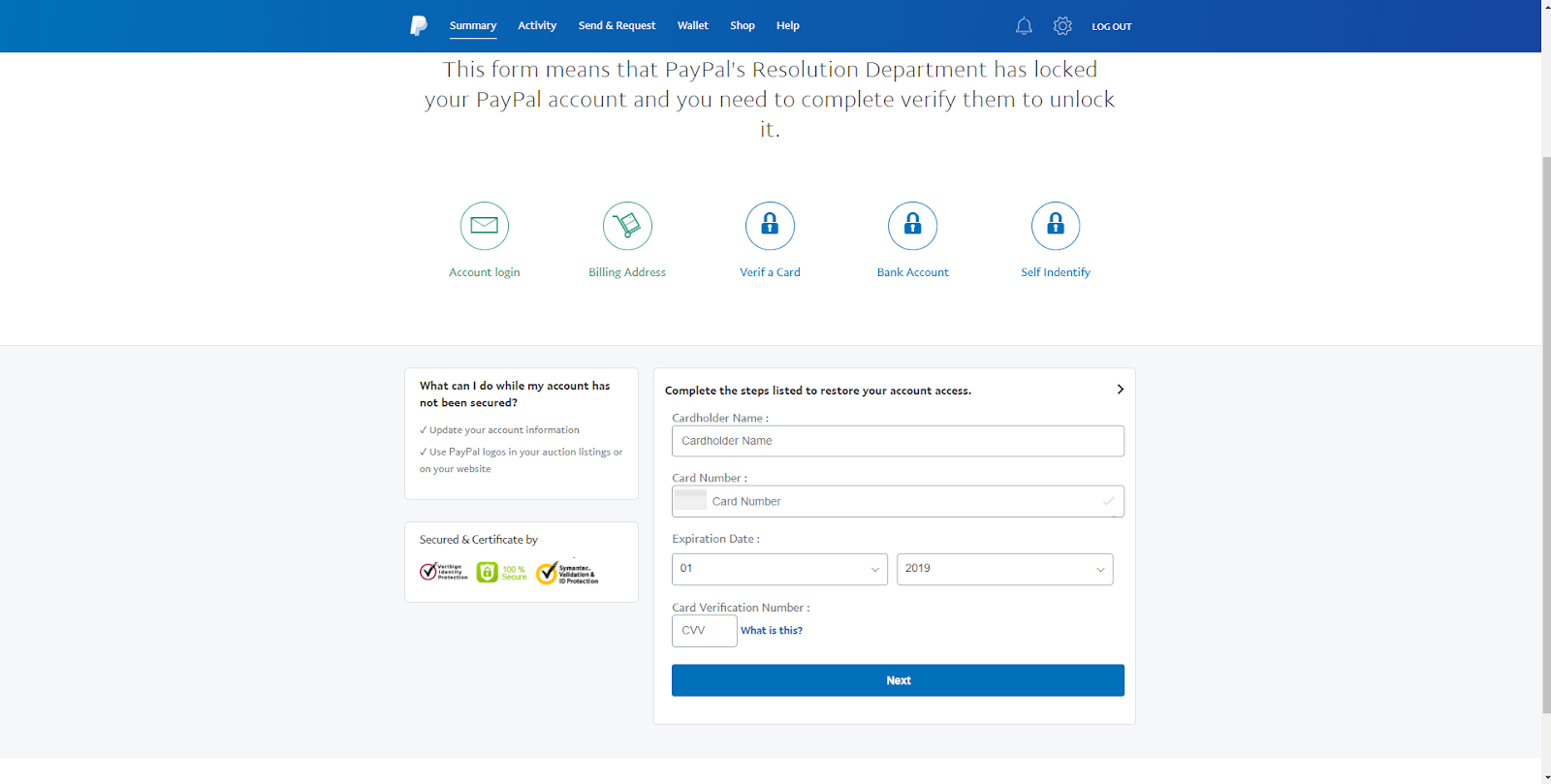

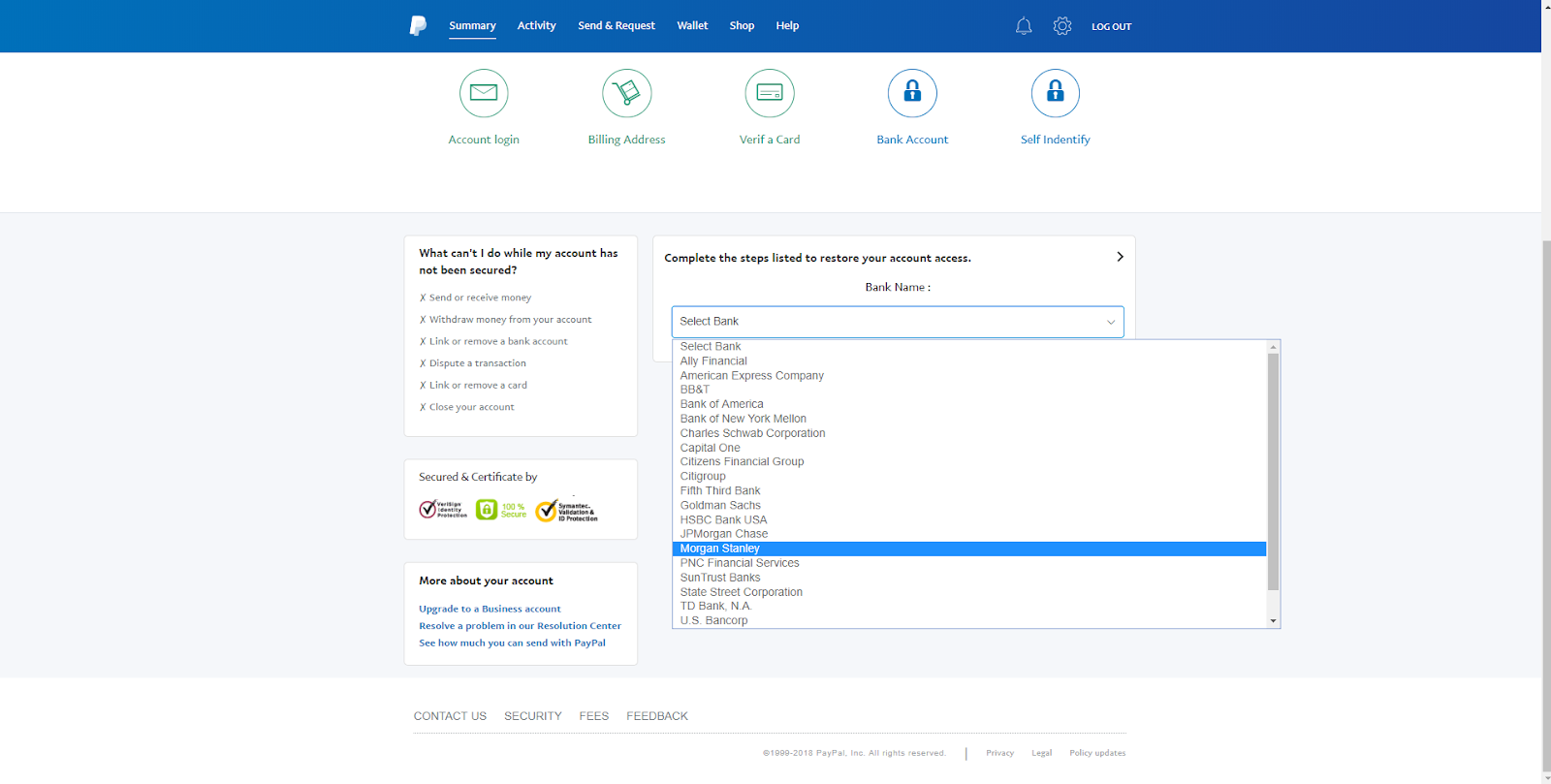
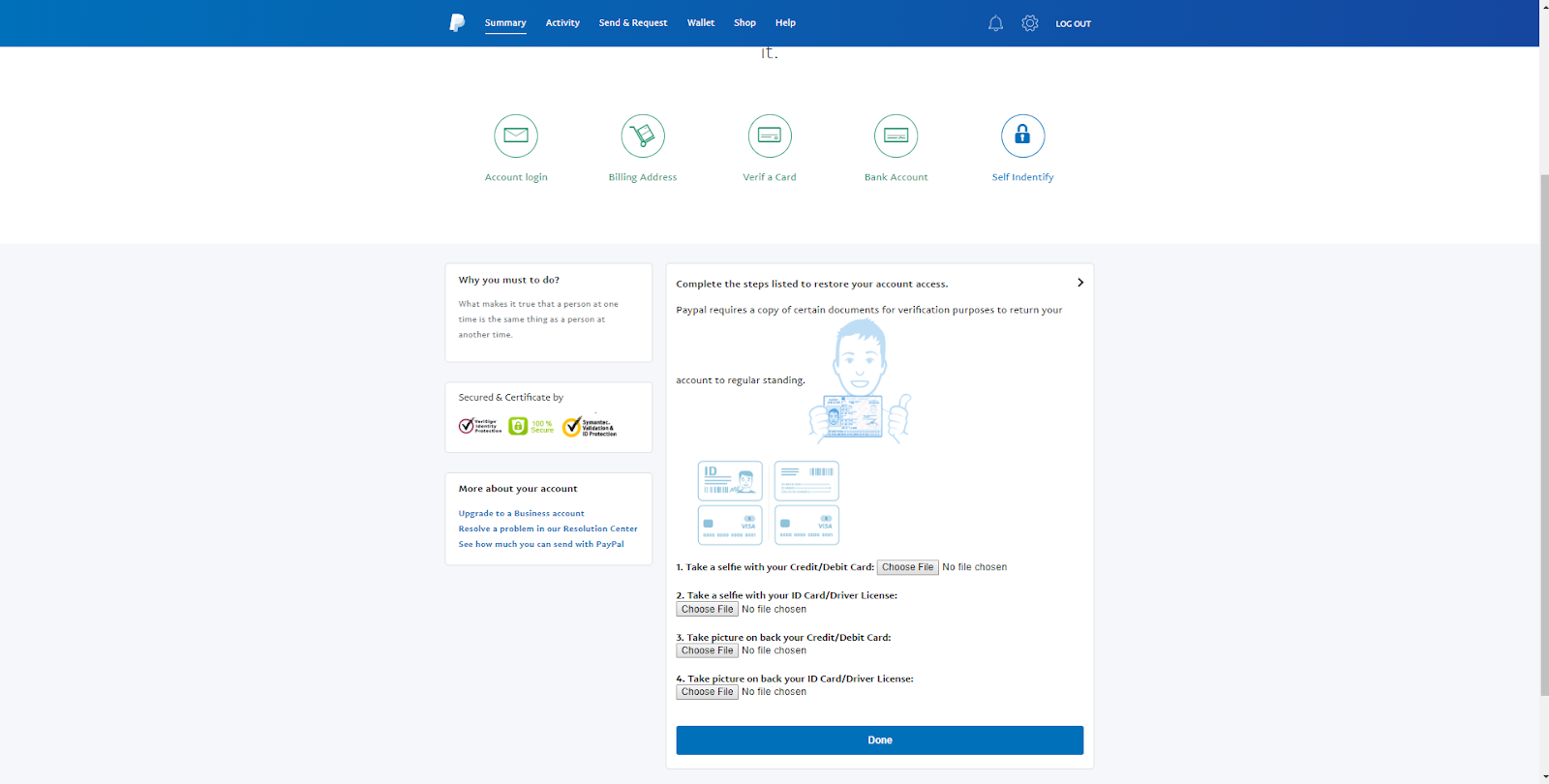
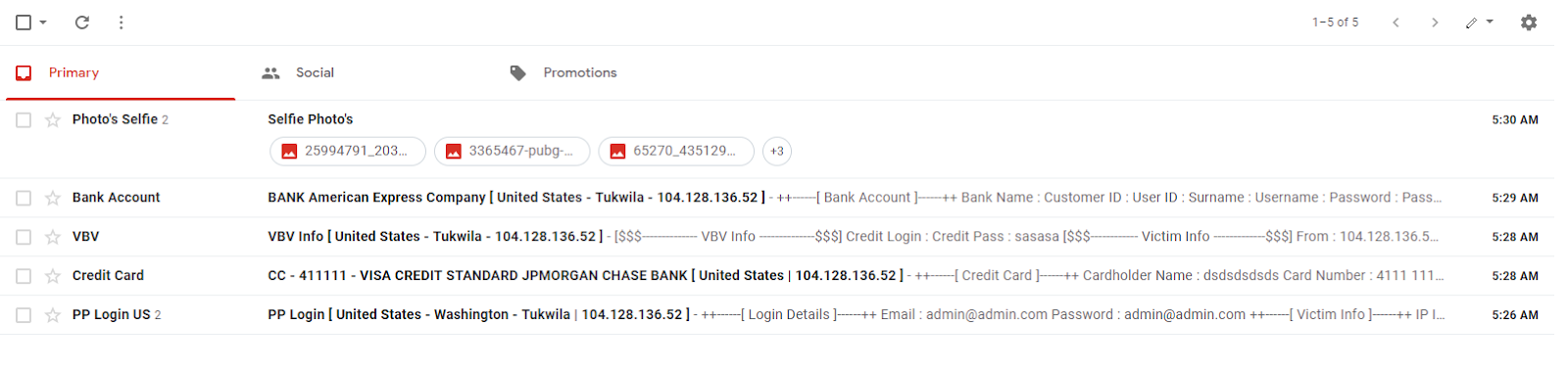
Password Reuse in 2020
Due to lax data storage policies such as failure to encrypt, including clear-text passwords in configuration files, failing to salt passwords, and improper partitioning, data breaches had become quite popular. Though all 50 states now have some sort of data accountability law to discourage this, that doesn’t change the fact that data from previous breaches is still retained in the hands of hackers.
A group going by the name of “GnosticPlayers” had accessed, publicly posted, and/or sold data belonging to dozens of websites. By simply performing credential stuffing attacks against GitHub (cross-checking usernames and passwords with sites similar to those breached), The group managed to acquire a whopping 932,000,000 accounts[2]. This should serve as a wake up call for those who fail to use a pseudorandom password generator for each account they create.
An even more concerning example came from a group called “ShinyHunters.” They used the same approach “GnosticPlayers” used, by targeting organization-level version control repository platforms like GitHub[3]. Given that most of the web is now powered by cloud computing platforms like Amazon Web Services, Microsoft Azure, and Google Cloud, almost every enterprise application contains a private API key that can be used for service theft. “ShinyHunters” also took advantage of accounts they got into that had databases (AWS RDS, GCLOUD SQL, ETC) and dumped them.

Rising Default Password Usage
Though just a few decades ago, a website was considered impressive if it had more than mere HTML and CSS, we now face the opposite problem, the more layers a website has, the larger an attack surface exist. Modern websites typically consist of several layers. For example, a common layout is a Java or C# backend, a middleware framework, technology to enable seamless data transfer like SignalR, and a front-end JavaScript framework such as React or Angular.
Most of these products have well-known default passwords that are only altered if the administrator manually changes them. Given the seemingly infinite layers in modern tech stacks, it’s no wonder that hackers often target these in the hopes that just a single layer was neglected.
This has led to devastating consequences. For example, a data warehousing and indexing site was breached by hackers in July. Some can hardly call it a “hack,” as it simply relied on the site’s poor and improper implementation of SonarQube utilizing the default username and password[4].
We anticipate that as web administrators continue to get even busier during the pandemic, these types of easy “smash and grab” attacks will become even more commonplace.
Targeting of IoT Devices
Though the “Internet of Things” has provided us with cutting-edge technology, it’s also brought about a wide-ranging series of vulnerabilities. So far, we’ve mostly only discussed enterprise-level and organizational attacks. However, there’s been a concerning uptick targeting of various personal IoT devices.
One of the most concerning and wide-reaching attacks occurred against the popular Amazon Ring doorbell camera. The strategy used in these attacks was identical to those in the attacks we discussed; credentials from previous breaches were run against the Ring system[5].
With at least hundreds of thousands of Ring credentials up for grabs, almost anyone using a hacking forum could hijack them. One of the most concerning elements of this attack is that there was no fiscal gain objective. The main reason hackers wanted Ring accounts was to violate privacy of those who own the cameras by recording audio and/or video or simply playing pranks on them.
A Simple Solution for a Serious Issue
It seems inane that these attacks could even occur in the modern era. For example, “Gnosticplayers” & “ShinyHunters” both acquired access to billions of user accounts with one of the oldest, and most common attack vectors (credential stuffing) thanks to developers & organizations violating basic cyber-security protocols: password recycling & weak passwords; which ultimately led to a lot of unnecessary damage and data-breaches.
We’ll look at how you can protect yourself against these types of attacks next. First, it’s a valid question to ask why these attacks were permitted to happen. Given that the vast majority of most stolen accounts stem from no-name sites, the answer is most likely two-pronged.
Smaller sites are less likely to use Captcha technology. This prevents bots from repeatedly running macros or scripts on sites. Just a simple human verification after three logins, for example, would have been an effective mitigation.
Of course, many credential stuffing attacks aren’t actually run through web pages. They can also be in the form of scripts that post a series of usernames and passwords and record which ones the API the site uses says are valid. This is why it’s prudent for organizations to place a request limit on clients by IP address. While anyone could bypass this with a VPN (/proxies), their progress would still be so greatly hindered that it likely wouldn’t be worth the effort. Additionally, the site would have far more time to detect and stop the attack.
Under-usage of MFA
Multi-factor authentication effectively halts credential-stuffing attacks when it’s universal and implemented correctly. Unfortunately, many so-called “security professionals” don’t understand the true meaning of the term. Many sites allow users to be sent their OTP (one-time pass code) through email (which is easier to compromise than it is to intercept something on a phone).
A true implementation of MFA requires something someone knows and something someone has, physically. A proper example would be requiring a username and password as well as a code sent through a text message (text-message based MFA can be compromised, through attacks known as "SIM Swapping". Everyday people should implement use of MFA even if it's SMS-based; it's better than nothing. However, high-level exec's, developers, and anyone who's willing to go a step further should make use of 2FA apps as it is the safest).
Had these services required a correct implementation of MFA to be used universally, there’s a very low chance any of these breaches could have occurred. However, consumers often don’t understand why they have to jump through extra hoops just to log in, making companies hesitant to do this.
Cit0Day: The Most Important Security Incident You’ve Never Heard Of
While small-time credential-stuffing attacks make the news regularly, more important cybersecurity incidents often slip under the radar. For those unfamiliar, Cit0Day.in used to be a site that essentially allowed users to find accounts with cracked hashes for a variety of sites. It was quite popular on many underground hacking forums.
This particular case is quite bizarre and still puzzles security researchers. Similar to its predecessors like WeLeakInfo, the site was essentially made by cyber-criminals for cyber-criminals. It rose to underground fame when its competitors’ sites were seized by the FBI.
First reported by cybersecurity watchdog KELA[6] through ZDNet, the site initial had a US Department of Justice and FBI joint take down notice. However, KELA’s analysis quickly showed that the take down notice was fabricated. Neither the FBI nor the DOJ announced any related arrests.
Around that time, 13.05 GB of cleartext usernames and passwords was uploaded to a file-hosting service. The link was shared on an underground Russian hacking site that we will not name for security reasons.
The file-hosting service removed it within hours, but the damage was done. 23,618 databases from different sites were now in the hands of hackers who didn’t have to pay a cent for them. KELA’s research shows that the people behind Cit0Day.in are still working in the illicit data trading business. They are simply being more discreet, dealing mostly through chat servers with trusted clients.
Some researchers believe that a rival hacking group hijacked the site and gave their databases out for free. However, no research group has publicly presented evidence to show what actually occurred.
The reason the Cit0Day.in data breach is so concerning is that it encompassed such a huge volume of accounts. They were already given out in a format ready for credential stuffing. Given that about 2/3 of people reuse their passwords[7] even though 91% surveyed stated that they knew it was an insecure practice, this is guaranteed to be the nexus of many data breaches in the future.
Protecting Yourself from Attacks
You’re probably getting the idea that cybersecurity didn’t fare too well this year. Before you worry about whether your own credentials are online, there are some quick mitigation steps you can take to preserve your assets and identity.
First and foremost, you should utilize a password generator to create passwords for accounts. The only reason you should use online password managers such as 1Password[8] or LastPass[9] is if you’re an everyday Joe who wants above average security. However, if you are a developer, Executive, or anyone who wants to take their security up a level, you should be using an offline password generator. A popular, open-source option for this is Password Tech (previously “PWGen”)[10]. Do not use online password managers! Regardless of security precautions, you’re adding to your own attack surface unnecessarily.
Next, you should simply assume that your passwords have been compromised and change them. The default settings on Password Tech are fine to use. If you’d like to know which ones are public knowledge, you can try out HaveIBeenPwned[11], a reputable site that simply has you enter your email, then informs you of hacked databases it’s in; or DeHashed[12]. Note that just because your email isn’t in a public database does not mean a cyber-criminal doesn’t have access.
This will probably take hours and isn’t the most fun task in the world, but it could save you money, time, and even your identity down the line. It’s the most effective defense against the increasingly popular practice of credential stuffing.
Where it’s offered, immediately enable Multi-factor authentication. Do not use your email as the “second factor” if prompted. 2FA Apps is the best route to take. A phone number that you know you’ll have for a while that can receive the text messages is the second best option. This will doubly protect you against having accounts stolen.
Be very cautious about what “smart technology” and IoT devices you choose to use. Since their inception, IoT devices have been notorious for being insecure. If at all possible, keep them within your local network. Remember, if they’re never connected to the Internet, nobody on the Internet will ever gain access to it.
Even with every precaution, there’s always a chance that through some new vulnerability, your information will be stolen. Enrolling in an alert system when your email, name, DOB, and/or SSN are found in a stolen database would be wise. This way, you’d be able to fix the issue before irreversible damage is caused. Many credit card companies offer this service to their customers free of cost.
2020 Security Stats
To keep you up to date, here are five key security statistics to know as 2020 ends.
-
Ever since COVID-19 was declared a federal disaster, the FBI stated that the rate of cyberattacks has increased by approximately 300%. [13]
-
Largely due to poor passwords, every 39 seconds, a networked computer is hacked. [14]
-
Though .exe files are often associated with malware, the most likely type of file to contain malware since 2018 has been Microsoft Office files. To avoid this, open this type of file on an online word processor. [15]
-
At the beginning of the year, Juniper Research predicted that cybercrime would end up costing people and businesses over $2 trillion this calendar year. The number has already surpassed that. Comparatively, in 2015, the total cost incurred due to cybercrime was about a quarter of that. [16]
-
From 2018 through 2020, the top target for Denial of Service attacks is the Financial Industry. [17]
Links & Sources:
- Katz , Or. “Threat Actors Recycling Phishing Kits in New Coronavirus (COVID-19) Campaigns .” - Akamai Security Intelligence and Threat Research Blog, Akamai. Accessed 23 Dec. 2020.
- Cimpanu, Catalin. “A Hacker Has Dumped Nearly One Billion User Records over the Past Two Months.” ZDNet. Accessed 23 Dec. 2020.
- “ShinyHunters Is a Hacking Group on a Data Breach Spree.” Wired. Accessed 23 Dec. 2020.
- FBI Flash, MU-000136-MW. Accessed 23 Dec. 2020.
- Cimpanu, Catalin. “Hackers Keep Dumping Ring Credentials Online ‘for the Giggles.’” ZDNet. Accessed 23 Dec. 2020.
- Cimpanu, Catalin. “23,600 Hacked Databases Have Leaked from a Defunct ‘data Breach Index’ Site.” ZDNet. Accessed 23 Dec. 2020.
- Inc, LogMeIn. “LastPass Psychology of Passwords Report Reveals 91% of People Know Password Reuse Is Insecure, Yet Two Thirds Do It Anyway.” GlobeNewswire News Room, 5 May 2020.
- “Password Manager for Families, Businesses, Teams.” 1Password. Accessed 23 Dec. 2020.
- #1 Password Manager & Vault App, Enterprise SSO & MFA | LastPass. Accessed 23 Dec. 2020.
- PWGen. Accessed 23 Dec. 2020.
- Have I Been Pwned. Accessed 23 Dec. 2020.
- DeHashed. Accessed 23 Dec. 2020.
- Walter, Jenna. “COVID-19 News: FBI Reports 300% Increase in Reported Cybercrimes.” IMC Grupo, 2 May 2020.
- Hackers Attack Every 39 Seconds. Accessed 23 Dec. 2020.
- Rapoza, Jim. "The Rise of Document-based Malware" Sophos. Accessed 23 Dec. 2020.
- Susan Morrow, Tony Crabtree. "The Future of Cybercrime & Security" Juniper Research. 27 Aug. 2019.
- "[state of the internet] / security A Year in Review" - Akamai Security Intelligence and Threat Research Blog, Akamai. Accessed 23 Dec. 2020.
